Remember „semi-persistent“ XSS-attacks?
It was in March of 2008 when I was writing about a third kind of Cross-Site-Scripting attacks, the so called „semi-persistent“ ones. One may prove this at my university’s public library ;-). But here I also have the digital version of it: http://www.erich-kachel.de/?p=181.
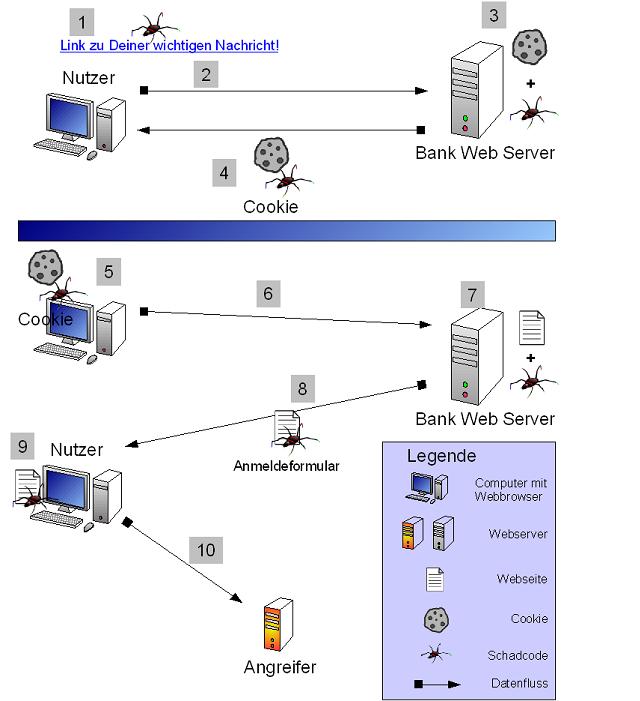
The chapter „Semi-Persistent“ explains a type of Cross-Site-Scripting attack which is neither persistent, nor reflexive. It is kind of both of these. Here is the picture with some Step-by-Step-explanation:
- The user uses an hyperlink (or an redirect or an form) with XSS-payload.
- He is redirected to his banking web application.
- The XSS-payload modifies the web page, so that malicious code infects a cookie.
- When this cookie is sent back to the user it contains malicious code.
- Some times later the user revisits the banking website.
- He now uses an official hyperlink or types in the URL. A safe way, isn’t it?
- The malicious cookie is automatically sent back and infects the website (a keylogger for example).
- Now the infected website is reaching the users client.
- Malicious code is now running at the users client.
- Captivated data is sent to attacker.
Today I am happy to see that this kind of attack is discussed in some more places. Hopefully more developers will keep this on mind and even encode cookie data safely before using it in direct output or even (*scary!*) in SQL queries.

Actually, people have been talking about these attacks since 2006 (when I started noticing them) and probably before that too, they just keep getting independently rediscovered. Such is life in infosec where there is no central repository of info.
I truly was surprised not to find *any* evidence of this kind of attack. Besides, I’d be very happy if you could post some (older) links here, if at hand.
There are probably other places, but I know I mentioned them in a talk I gave at the end of 2007; slides 8 & 9 in http://events.ccc.de/congress/2007/Fahrplan/attachments/1054_unusual_web_bugs.pdf
And I found the $_REQUEST thing in 06, and though I didn’t mention xss per se, I was using it for persistence: http://kuza55.blogspot.com/2006/03/request-variable-fixation.html
Can’t think of any other examples off the top of my head though.